In my previous post, I provided instructions on installing the Hidden Eye tool. If you haven't installed it yet, please do so before proceeding. In this post, I'll demonstrate how to utilize the Hidden Eye tool to potentially assess social media account security.
There are numerous tools available for Termux designed for replicating login pages. One of the simpler options is ShellPhish, but Hidden Eye stands out as an advanced tool in this category. It includes replicas of popular websites and offers more options compared to others. In this post, we'll focus on a method to replicate Instagram login pages using the Hidden Eye tool. However, feel free to explore other options as the steps remain the same
Requirements:
1) Download Termux On your phone.[Download]
2) Install Hidden Eye in Termux.[Install]
Step 2:
Now You have to Select The Name of Social media like Facebook, Instagram. To select a social media you have to type the number before it and Press Enter. In this post, I am selecting Instagram.
Type 8 to select Instagram.
Step 3:
Now you can select any option you want, it depends upon your social engineering tactics All the options are really incredible I will create a separate post on some of the best options. But for simple Instagram page, You can select the first option(1) and press Enter.
Step 4:
Step 5:
Requirements:
1) Download Termux On your phone.[Download]
2) Install Hidden Eye in Termux.[Install]
NOTE: This post is only for educational purposes. This site and I do not support any criminal activity. If you are doing any sort of misuse of this information This site is not responsible for that. THIS SITE ONLY SUPPORT ETHICAL HACKING.
Use Hidden Eye Tool in Termux:
Step 1:
Open hidden I tool so you can see this menu if you don't know how to open this menu just follow my previous post [Install and Use Hidden Eye In termux].Step 2:
Now You have to Select The Name of Social media like Facebook, Instagram. To select a social media you have to type the number before it and Press Enter. In this post, I am selecting Instagram.
Type 8 to select Instagram.
Step 3:
Now you can select any option you want, it depends upon your social engineering tactics All the options are really incredible I will create a separate post on some of the best options. But for simple Instagram page, You can select the first option(1) and press Enter.
Step 4:
A keylogger is a tool that captures the Keys that you have pressed. If we will add keylogger on the website your will see all keys the recipent is pressing and it will give us some extra information. sometimes this feature doesn't work properly but it's just an addon so it doesn't matter much. Type Y and press Enter. If it does not work then try pressing N.
Step 5:
Now it will ask you [*]Do You Want to Enable CloudFare Protection?
If you enable Cloudfare Protection Whenever anyone will open the Link, They will encounter first with this Cloudfare Protection Page. Most of the popular site use CloudFare Protection to save their site form DDOS attacks. Here is the Screen Shot of the Cloud fare protection.[ScreenShort].
I am not going to enable this. (Because real Instagram doesn't use this feature.)
Type N and press Enter.
If you enable Cloudfare Protection Whenever anyone will open the Link, They will encounter first with this Cloudfare Protection Page. Most of the popular site use CloudFare Protection to save their site form DDOS attacks. Here is the Screen Shot of the Cloud fare protection.[ScreenShort].
I am not going to enable this. (Because real Instagram doesn't use this feature.)
Type N and press Enter.
Step 6:
Capture data to Email?
This option is a little complicated Because it will ask your Email and Password as well as you have to disable the 2-factor authentication. in most of the cases, this Option is not useful because you will get the Credentials in your terminal anyway.
Type N and press Enter.
This option is a little complicated Because it will ask your Email and Password as well as you have to disable the 2-factor authentication. in most of the cases, this Option is not useful because you will get the Credentials in your terminal anyway.
Type N and press Enter.
Step 7:
Next, you'll need to enter a URL. After the recipient clicks on the login button, they'll be redirected to the link you provide in this step. You have the flexibility to input any link you prefer. However, to avoid detection, consider using the link to Instagram. This way, if the recipient encounters any issues, they may perceive it as a bug and proceed to enter their credentials on the authentic Instagram website, successfully logging in.
Enter www.Instagram.com and press Enter.
Step 8:
Now you have to type any available Port, for Port Forwarding.
Just type 1275 and press Enter.
Step 9:
Now you have to select the Host server(The post Forwarding method) some servers in this Tool are not working and some of them are not getting installed Properly, so we will use LocalHost now. Select the first option(0) and press Enter.
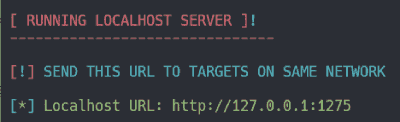
Step 10:
Now The localhost setup is Completed, and this will only work in local area network. to make it go live, we have to do port forwarding. Copy the localhost URL.
Step 11:
Now to create a tunnel from our local host to the internet we will use a single command. First of all open a new session in your termux(to open a new session you just have to swipe from left side of your screen to the right in termux terminal and then click on new session) and just copy and paste the below command but make sure to change your port number if you have a different one.
Step 12:
The command above will initiate a cloudflared tunnel, and you'll receive a link, as illustrated in the screenshot below. Simply copy that link and send it to the recipient. (Please refrain from engaging in illegal phishing activities.)
Step 13:
Now, wait for the recipient to click on the link. They will be directed to the fake Instagram page. If the recipient enters their information and clicks on the login button, you will receive the username and password of the recipient on your terminal.
Fix portforwarding issue (read this post if cloudflared is not giving you link)
Read this Post : [ Termux Maskphish : Mask URL in Termux ]Conclusion:
Hidden Eye is a potent tool that constantly evolves, ensuring its effectiveness. Exploring its diverse features can be highly beneficial. In future posts, I'll delve into these features to help you harness its full potential. Remember, this post is for educational purposes only. Engaging in unethical activities is strongly discouraged, as digital trails are easily traceable. For further insights, explore [Get Exact Location Using Termux 📍] . If you encounter any issues, feel free to ask in the comments. Thank you for reading, and always prioritize ethical behavior. Stay ethical! 👾















.png)




29 Comments
Hy does this way work also on facebook by replacing Instagram by Facebook?
ReplyDeleteYes, you can select any social media you want.
DeleteHello saad khan, please I need your help,
ReplyDeletePlease chat me up on my WhatsApp number: +2347088306308
I would appreciate it if you message,
That's my WhatsApp number above,
Thanks,
i can contact you only if you will tell me the reason
DeleteYes
DeleteHello, what if you have already installed hidden eye ? Where do you start?
ReplyDeleteyou need to start from this post
DeleteHello, in hidden eye when victim click on link that time they need to login an social app aur hidden eye automatically fatch user name password?
ReplyDeleteThey have to log in using this link then you will get the info.
DeleteNice article for aspiring ethical hacker like me.keep it up
ReplyDeleteThank, i really appreciate it. <3
DeleteHow do you open HiddenEye I already have it installed.
ReplyDeleteYou have to restart termux then you need to use cd command to get into the HiddenEye-Legacy folder, and then you need to run python HiddenEye.py
DeleteHow can i open some blocked
ReplyDeletehacking websites
what do you mean?
DeleteHey brother please help me my ngrok link is not working in my victim's phone it's only working in my phone it says server refused to connect please reply me on whatsapp I am there as 7340126564
ReplyDeleteNow i have updated the commands so it will work.
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteSir for the process of to get folowers on Instagram
ReplyDeleteIn step 3 of this post just select the 2nd option.
Deletei need to learn
ReplyDeleteYep, keep studying, If you want to learn something specific then let me know on instagram.
DeleteBro can you hack pubg uc
ReplyDeleteNope, that's illegal :)
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteI need ur help pls respond brother
ReplyDeleteBrother, u should contact me on Instagram.
Deletesir where i have to send the link of ngrok (through the sms,whatsapp or Instagram msg)
ReplyDeleteEverything works bro. Use maskphish tool so it won't look so fishy 😂
Delete